In the prior post we created the primary domain controller. In this article we will configure Active Directory and add a second domain controller.
In a later post we’ll set up ADFS and Azure Active Directory (AAD)- both of which are required for Dynamics 365 for Finance and Operations.
Add an OU and Domain Admin Account
25. Open the Active Directory Administrative Center
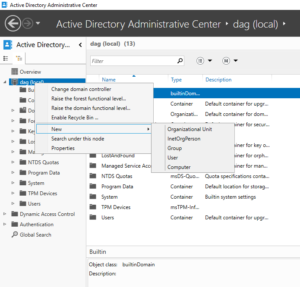
26. Right-click your domain name > New > Organization Unit
27. Type in “Lab” for the name and accept the defaults for the other fields.
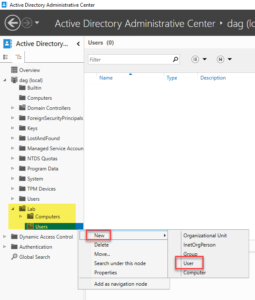
28. Create two organization units (OUs) underneath, one for computers, another for users.
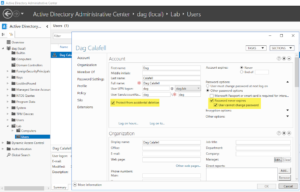
29. Create a user under the Users OU.
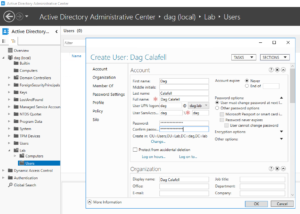
30. Fill out first name, last name, user SamAccount, and passwords.
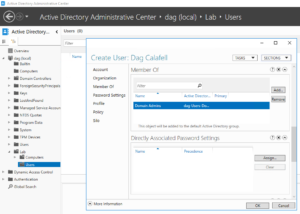
31. Add the user to the “Domain Administrators” group on the “Member Of” group.
32. (Optional) This is a test domain, so you can change the account to not expire the password (not recommended in real environments) and prevent the account from accidental deletion.
Add the second VM to the existing domain
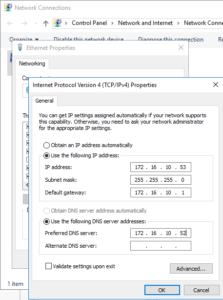
33. Perform steps 10 through 13 on the second VM, then set a static IP with the DNS server referencing the first virtual machine. This is necessary because Active Directory creates SRV DNS records which need to be referenced to join computers to the domain.
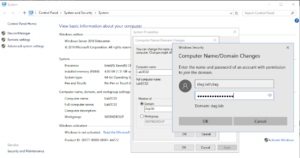
34. Join the second virtual machine to the domain (requires a restart).
35. The installation of the role is the same, however we will configure/promote the AD server differently. Complete steps 17 and 18 above on the second VM.
36. In server Manager, click on the pending notifications and then “Promote this server to a domain controller”
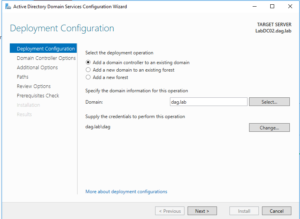
37. We will use the “Add a domain controller to an existing domain” option, using the credentials of the user created earlier.
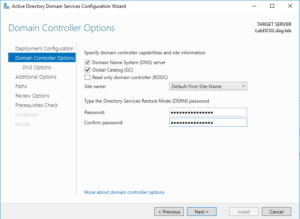
38. Specify the same Directory Services Restore Mode (DSRM) password as used on the other server.
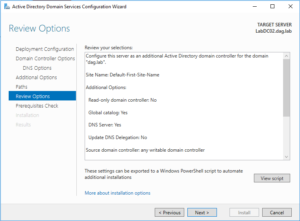
39. Accept the default settings for the rest of the wizard and “Updating DNS delegation” is not necessary. Click Install.
40. The server should reboot. Finally, kick off Windows updates, as per the usual.
Congratulations we now have a two-DC Active Directory domain!



Leave A Comment